
Threat Hunting: The next evolution in cybersecurity
How you can proactively pursue, discover, and stop cyberthreats in their tracks with Cisco Secure Endpoint and SecureX
1 in 4 companies risk a major security breach in the next 24 months
Get this ebook to learn:
- How threat hunting is different than traditional cybersecurity
- The three categories of threat hunting
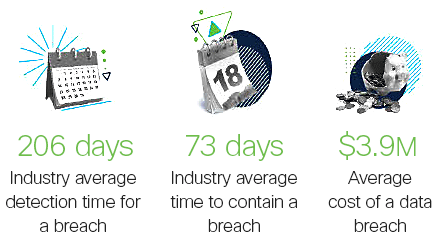
- Measurable cybersecurity improvements achieved as a result of threat hunting
Through Cisco Secure Endpoint Premier with SecureX Threat Hunting, organizations of any size can now apply an established, mature threat hunting practice to their environment at a fraction of the cost and time of doing it themselves.
Get the ebook now
* Required